Protect Your Digital Assets from Evolving Threats
In today's increasingly connected world, cyber threats are constantly evolving. FCL provides comprehensive security solutions to protect your organization's critical data, systems, and reputation.

Comprehensive Security Services
Our expert team provides end-to-end security solutions tailored to your organization's unique needs and risk profile.
Information Security Audits
Comprehensive assessment of your security posture to identify vulnerabilities and compliance gaps.
Data Security Solutions
Robust solutions to protect sensitive data across your organization with encryption, tokenization, and access controls.
Identity & Access Management
Secure management of digital identities and user access to critical resources and applications.
Risk Assessment & Management
Proactive identification and mitigation of security risks before they can impact your business.
Compliance Management
Ensure adherence to industry standards and regulations like ISO 27001, GDPR, and PCI DSS.
Incident Response Planning
Develop and test response strategies to minimize impact and recovery time during security incidents.
Network Security
Protect your network infrastructure from unauthorized access and cyber threats.
Cloud Security
Secure your cloud environment and applications against emerging threats and vulnerabilities.
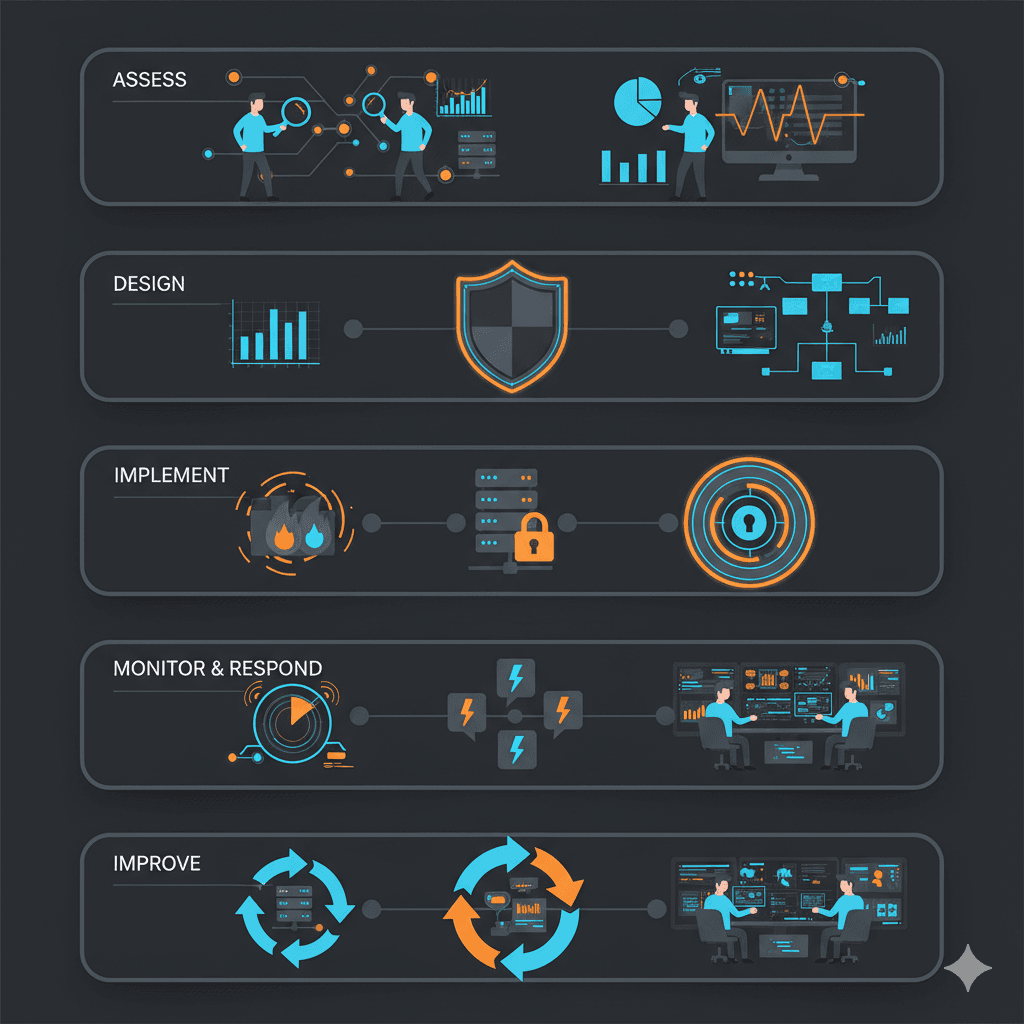
Our Security Approach
We follow a proven methodology that ensures comprehensive protection while minimizing disruption to your business operations.
Assess
Comprehensive evaluation of your current security posture and identification of vulnerabilities.
Design
Development of tailored security strategies and controls based on your specific needs and risk profile.
Implement
Deployment of security measures, policies, and technologies to protect critical assets.
Monitor & Respond
Continuous security monitoring, threat detection, and rapid incident response.
Improve
Regular reviews and updates to security measures to address evolving threats and business needs.
Why Choose FCL for Security
Our comprehensive approach combines cutting-edge technology with deep expertise to deliver security solutions that actually work.
Comprehensive Protection
End-to-end security solutions that protect your entire digital ecosystem from evolving threats.
Data-Driven Approach
Security strategies based on real-world threat intelligence and your organization's specific risk profile.
Expert Security Team
Certified security professionals with experience across multiple industries and security frameworks.
Continuous Monitoring
24/7 threat monitoring and detection to identify and respond to security events in real-time.
Our Security Partners & Technologies
We leverage industry-leading security technologies to provide robust protection.

Sophos

Microsoft

Red Hat Security

F5

NGINX
Client Success Stories
See how we've helped organizations across different industries strengthen their security posture and protect their critical assets.
Finance Organization
Enterprise Company
Security Challenge:
Compliance with PCI DSS and financial regulations while securing sensitive customer data.
FCL Solution:
- Comprehensive security assessment and risk analysis
- Implementation of tailored security controls and monitoring
- Staff training on security awareness and best practices
Healthcare Organization
Mid-size Company
Security Challenge:
Protecting patient information while ensuring compliance with HIPAA requirements.
FCL Solution:
- Comprehensive security assessment and risk analysis
- Implementation of tailored security controls and monitoring
- Staff training on security awareness and best practices
Manufacturing Organization
Enterprise Company
Security Challenge:
Securing industrial control systems and intellectual property from cyber threats.
FCL Solution:
- Comprehensive security assessment and risk analysis
- Implementation of tailored security controls and monitoring
- Staff training on security awareness and best practices
Government Organization
Large Company
Security Challenge:
Implementing comprehensive security framework across multiple departments and services.
FCL Solution:
- Comprehensive security assessment and risk analysis
- Implementation of tailored security controls and monitoring
- Staff training on security awareness and best practices
Security Assessments
Get a comprehensive view of your security posture with our detailed assessments and recommendations.
Vulnerability Assessment
Identify and prioritize security vulnerabilities across your IT infrastructure.
Penetration Testing
Simulate real-world attacks to test your defenses and identify security gaps.
Security Architecture Review
Evaluate your security architecture against industry best practices and standards.
Compliance Readiness Assessment
Prepare for compliance audits with a detailed analysis of your security controls.
Common Security Gaps We Identify
Outdated software and missing security patches
Weak authentication and access controls
Inadequate encryption of sensitive data
Insufficient security monitoring and alerting
Lack of employee security awareness training
Security Training & Education
Empower your team with the knowledge and skills needed to maintain a strong security posture and respond effectively to threats.
Employee Security Awareness
Interactive training programs that teach employees to recognize and respond to common security threats like phishing, social engineering, and malware.
- Phishing simulation and training
- Social engineering awareness
- Password security best practices
- Malware detection and prevention
Security Policy & Compliance
Development and implementation of security policies and procedures to ensure compliance with industry regulations and best practices.
- Security policy development
- Compliance framework implementation
- Risk management procedures
- Regulatory compliance assessments
- Data protection and privacy controls